2. Sensitive data exposure
Data can be exposed due to human error when a negligent employee uploads it to a public database or a website. But this security vulnerability type can also be supported by internal processes that actually allow an unauthorized employee to gain access and manipulate sensitive data.
Egress, a cybersecurity firm, conducted a survey uncovering that
83% of the US organizations have accidentally exposed sensitive data through email, file sharing, collaboration software, and messaging apps.
3. Insufficient transport layer protection
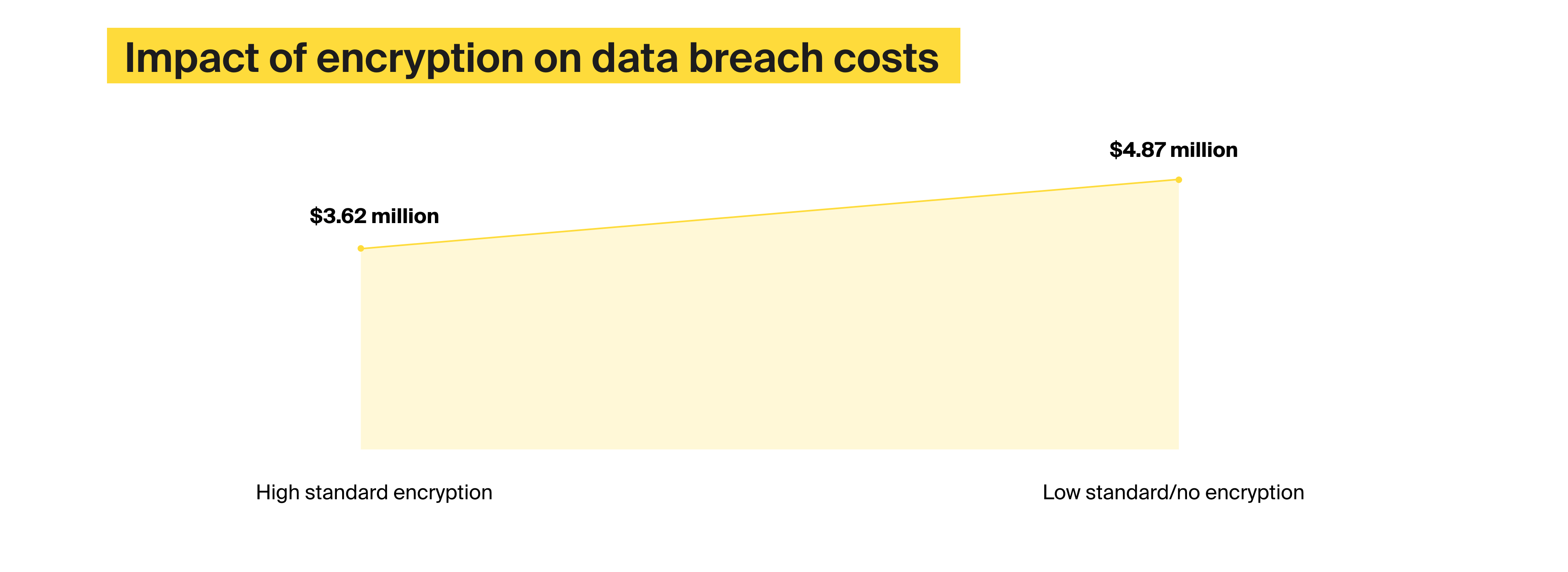
This type of vulnerability deals with information exchange between the client and the server application. Such information can contain sensitive data, including user credentials and credit card details. When data transportation is not secured, the communication can be intercepted, and attackers can gain access to the data and decipher the encryption if weak algorithms are used.
4. Misconfigured system components and risky interactions
Incorrectly configuring components and interactions between them is another security issue that we often encounter. For instance, while setting up an IT system, the administrator forgets to override the manufacturer’s default settings and disable directory listings, leaving the system exposed. Another example is forgetting to restrict access to outside devices.
Speaking of interactions, it is advisable for applications to adopt a zero-trust approach and view every input as risky before it is verified and proven to be legitimate. This will help avoid attacks, such as cross-site scripting, where attackers infuse an application with untrusted data.
This aspect is particularly relevant to cloud-based solutions. One research reported that server misconfigurations contributed to
200 cloud breaches in two years. Another study shows that around
70% of cloud security breaches start with faulty architecture. As an example, a misconfigured AWS storage bucket
exposed 750,000 birth certificate applications in the US in 2019.
5. Weak server-side control
This security vulnerability type stands for everything that can go wrong on the server side, from poor authentication to security misconfigurations that enable attacks, such as cross-site request forgery where some user’s browser issues unauthorized actions to the server without that user’s knowledge.
For instance, misconfiguration in a database server can result in data becoming accessible through a basic web search. And if it contains admin credentials, then intruders can gain access to the rest of the system.
6. Remote code execution
This means that software security vulnerabilities presented by your system enable intruders to execute malicious code over the internet on your devices. For example, when an employee clicks on an email link on a third-party website, the hacker behind this setup injects the victim’s computer with malware and assumes control from there. The outsider can access sensitive data or lock the machine and demand ransom.
7. Known OS-based vulnerabilities
Every operating system has its list of software vulnerabilities. Some lists are published online for everyone to see. For example, here is the list of top 10
Windows 10 OS weaknesses, and here is the corresponding
listing for OS X. It is up to security teams to review these points and address them to minimize the openings for attacks.
8. Running scripts without virus check
This is a common security vulnerability type that is present in certain web browsers. For instance, Safari allows running “trusted” scripts without explicit user permission. Hackers tend to exploit this weakness by attempting to run a malicious piece of code that can be confused with a “safe” script. Luckily, it’s often possible to disable this “feature.”
9. Weak credentialing
Intruders can gain access by brute forcing users’ credentials. This is especially easy when the password “123456” alone is used by over
23 million people. This is in addition to passwords, such as “admin”, “password”, and “qwerty”, that are also common and rather easy to hack.
This type of software vulnerability is regarded as human-made, but businesses can implement measures that would force employees to choose stronger options and change their credentials often enough. This is crucial, given the role that weak credentialing plays in system security. Statistics show that 80% of security breaches were enabled by weak passwords, and that
61% of users tend to utilize one security phrase for multiple services.
10. Using components with known vulnerabilities
Deploying third-party components, such as libraries, APIs, datasets, and frameworks, can significantly reduce the effort required to have your system up and running. But it can also introduce vulnerabilities. It’s important to remain diligent and evaluate these components to make sure they don’t leave any backdoors open to access sensitive data.
Even downloading and using third-party images could be dangerous. In 2021, 30 Docker Hub images with a download volume of 20 million, were
deployed to spread cryptomining malware.
11. Insecure design
This is a relatively new security vulnerability type that appeared on OWASP in 2021. The organization calls for secure design patterns, threat modeling, and reference architecture to eliminate weaknesses from the very beginning.
Secure design is a methodology that constantly evaluates threats and ensures the code’s robustness. It encourages systematic testing against known attack methods. It views security as an essential part of software development, not as an add-on or a nice-to-have feature.
12. Security bugs in APIs
Application programming interfaces (APIs) allow software components to interact with each other, which is an essential part of an IT system. However, APIs with weak security measures can open multiple loopholes, such as broken authentication and permit code injection and other malicious practices.
For instance, a recklessly built API, which relies on the client side to filter information before presenting it to users, can expose data, making it available for grabs. Sensitive data must be filtered at the server side. Here’s another example of this security vulnerability type: if an API doesn’t restrict the number of incoming requests, it can open the opportunity for Denial of Services (DoS) attacks.
Here is the OWASP list of the top
10 API-related security vulnerabilities for your consideration.
Insecure APIs opened the door to many attacks in the past years. One infamous example comes from LinkedIn, as a malicious actor used the platform’s authentication-free API to download data of
700 million users. Using a similar API breach, an intruder retrieved information on
1.3 million Clubhouse users and published it on a hacker forum.
13. Inadequate authentication
Weak authentication measures allow hackers to exploit the “forgot password” option to reset accounts or initiate an account takeover attack. It helps the intruder when the authentication question is something like the user’s birthdate or pet name, as this is publicly available information thanks to social media.
Following a multi-factor authentication process will increase security. Sadly, research shows that only
26% of the US companies use this strong authentication method.
14. Insufficient monitoring and logs
Logs store data on system events, network activities, and user actions. By monitoring logs, security teams can observe all the activities that took place recently and identify suspicious events. If logs are not reviewed systematically, this creates an information gap where software vulnerabilities and malicious activities remain undetected.
15. Superuser privileges
The fewer data a user can access, the less damage their account can do if compromised. However, some businesses still negligently grant superuser privileges left and right and fail to restrict employees’ access to what they need to fulfill their everyday duties. If an intruder takes hold of an admin-level account, they can disable anti-virus software and firewall, install harmful apps, take ownership of files, etc.
According to research,
74% of data breaches start with abusing privileged credentials.
16. Outdated software
Most businesses realize that a timely software update is key to a secure system. However, it seems like only a few actually follow this practice.
Cybernews reports on a recent study that investigates software update frequency. This research was conducted over an 18 months period, and it discovered that 95% of the websites examined actually run on outdated software with known vulnerabilities. The research team also discovered that an average software product is typically four years behind its latest patch.
Moreover, Kaspersky determined that companies running outdated software are likely to incur
47% more costs in case of a breach.
To give an example, the Marriott hotel chain had
500 million data records compromised in a security breach that resulted from an unpatched software.
17. Vulnerabilities in source code
This code vulnerabilities creep in during software development. For example, a program might transmit sensitive data without encryption or use a randomized string, which is not actually random. Such errors are often caught during the software testing phase.
According to a recent Secure Code Warrior Survey,
86% of the participating developers admitted that they don’t view application security as a top priority when writing a code, with 36% attributing this to tight deadlines. The survey also revealed that 33% of the respondents don’t even understand what makes their code vulnerable.
18. SQL injection
This security vulnerability type is relevant to websites and applications powered by Structured Query Language (SQL). It allows the attacker to alter user-supplied SQL statements and trick the interpreter to execute unintended commands and grant access to the database. This way, intruders can manipulate sensitive data by replacing/deleting/modifying sensitive fields.
This is a rather old vulnerability that accounted for over
65% of attacks on software apps already back in 2019.